OWASP Foundation/ OWASP Top Ten
Forget about the security risk in web application and development, OWASP Top 10 gives full security to your company’s developers and helps in generating secure code.
Who is the OWASP Foundation? (OWASP organization)
The Open Web Application Security Project (OWASP) Foundation is a non-profitable organization that works to improve the security of software developers on the web. OWASP foundation runs an online platform where thousands of people serve training, free education, and guidance to the open-source software projects leads many conferences and webinars. This OWASP Foundation is a resource for developers and technologists t secure the web.
This organization provides services that include:
- Tools and Resources
- Community and Networking
- Education and Training
- Conferences and Webinars
Now its been 20 years since developers, volunteers, corporations helps to run the OWASP Foundation successfully. Click here to donate, join, and becomes a contributor.
What is OWASP?
OWASP is a team of highly influential people who provides security to software and web application without charging a single penny or service. An ‘open community’ model, OWASP provides free access and free security to your software and applications. Everyone can access, read, write and update the code and can contribute to events, development, and online chats.
An OWASP is a non-profitable, freely available foundation and is mainly dedicated to providing security of software. OWASP offers everything like tools, videos, guidelines, videos, events, webinars for free. A team of well-experienced and knowledgeable people gives all-in-one web application security.
What is OWASP Top 10?
If you are aware of OWASP then you definitely know the fact of OWASP Top 10, still we will give you an outline of OWASP Top 10 in this article. OWASP Top 10 is the online document that was very first launched in 2003. The main purpose and motto of this document are to cover Top 10 most critical web application security risks and vulnerabilities. Later we had the next version that is known for OWASP Top 10 2017. Recently in September 2021, OWASP releases its new version that is OWASP Top 10 2021.
The purpose of this report document is to provide the application and web developer security professionals insights into the most relevant security risk so that in the future the expert can minimize the security risk of the data.
Overview of OWASP Top 10 and how it works
OWASP always maintains its list of top 10 security risks. Every after 2-3 years it updates its database and security risk factor as per the revolutions that take place in AppSec Market. Auditors target its top 10 risk factors to its Software Development Life Cycle (SDLC), which shows overall commitment for secure web application development.
A long waited OWASP update was finally released in September 2021. After 8 long years, OWASP comes with its highly appreciated and awaited update OWASP Top 10 2021. As the technology grows the risks of vulnerabilities and security increase, so any application or technology must be updated to tackle the upcoming threads in the industry.
In the below figure, we can clearly see what was the OWASP Top 10 2017 and 2021. Many latest updated vulnerabilities are added in the 2021 update. So here we explain each changes one by one.
Software development organizations should accept this document in response to make it more secure their applications globally.
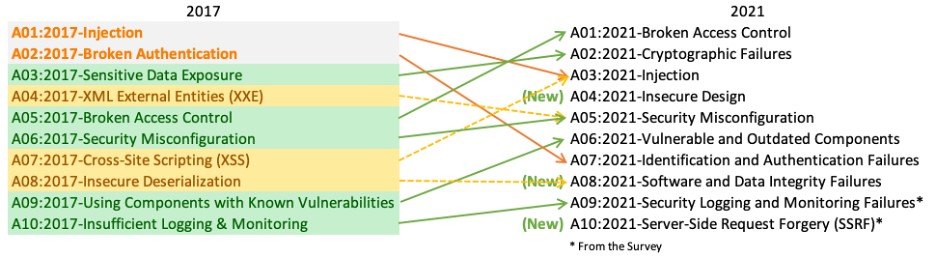
Comparison bet OWASP Top 10 2017 and 2021
Here we will cover the security risk reported in the Top 10 2017 document
OWASP Top 10 2017 list of Risk Document
As shown in the above figure we will discuss here each security risk mentioned in the 2017 OWASP update.
A01:2017-Injection:
Injection attacks can happen when irrelevant or inappropriate data get added to the application. Many times it happens that untrusted data get sent to the code interpreter or developer as input. For example, an attacker could send an SQL database. And if this code is getting executed in a web application this is known as an SQL injection attack. It can be prevented by giving proper authentication, validation, and sanitizing the incoming data. Database admin can set control on various incoming data to be added.
A02:2017-Broken Authentication
It is found that vulnerabilities in login can be the reason for the attackers to enter and access the user account. Many times this attack can take place on the admin’s account and here the attacker gets the 1000s of the user’s credentials. By using any script the matches the user ID and passwords of various users and attack your whole software. To avoid such risk OWASP offers you two-factor authentication (2FA) and it also suggests imposing the time limitation while logging or repeated login attempts.
A03:2017- Sensitive Data Exposure
Many times it happens that web applications dose not secure sensitive data such as financial data or user credentials. In such conditions risk factor of attacking get increases. To avoid such circumstances, the top 10 risk documents guide you with data encryption techniques. Encrypt all your sensitive data using encryption protocol on your websites and disable the caching of any sensitive information.
A04:2017-XML External Entities
The web applications that parse XML input are mostly attacked by XML entities. XML inputs refer to external entities that can attempt to exploit in the parser. Extensible Markup Language is both machine-readable and human-readable, because of this complexity attacks can occur.
A05:2017-Broken Access Control
Access control can be secured by imposing the two-way authorization to the various authors by the admin.
A06:2017-Security Misconfiguration
Security misconfiguration is the most common risk of the OWASP Top 10 risk. An application could show some error that is not relevant for the user and this can be avoided by removing unused code from the software.
A07:2017- Cross-Site-Scripting
These type of vulnerabilities occurs when a web application allows a user or client to add external code to the source. For example; if an attacker sends an email containing a malicious link to the bank persons who handle the software and if that person runs that link to the software, the malicious JavaScript code can be the reason to attack the application.
A08:2017- Insecure Deserialization
This type of error can occur when a developer uses the same data for different purposes. Serialization and deserialization of data cause this threat. Insecure deserialization of data can result in very serious risks like DDoS attacks and remote code run track. This kind of attack can be prohibited by avoiding insecure deserialization.
A09:2017- Using Components With Known Vulnerabilities
Today in web application development many readymade components are available. Developers use such small components for the front-end framework and or landing page framework. Developer picks bulk of readymade data from any client or directly from the web. The chances of vulnerabilities may increase by using such unauthorized vendors. To avoid such attacks developers much use their own generated applications whether it takes a little extra time to deliver final output.
A010:2017- Insufficient Logging And Monitoring
It is seen that many application developers do not take enough steps to detect data breaches. To detect data breaches it takes an average of 200 days and that much time the attackers cause lots of damage to your original application. OWASP Top 10 document is here to help you to implement incidence response, logging, and monitoring plans so that developers can be aware of the attacks.
OWASP Top 10 2021 list of Risk Document / Top 10 vulnerabilities
The above figure mentioned that, there are some significant changes are done In the 2017 document, some risks go up some risks are going down and some are combined in 3 new categories.
Let’s have a look at OWASP Top 10 2021 one by one
A01:2021- Broken Access Control
In the 2017 update, we have seen that the broken access control risk factor lays at 5th most important security threat. IN 2021 Update it jump to the first position since 94% of applications tested and found broken access control. Among the 34 Common Weakness Enumerations (CWEs), broken access control was identified as the most significant security threat.
A02:2021- Cryptographic Failure
The cryptographic Failure is nothing but Sensitive Data Exposure, in the 2017 update it was listed at 3rd place and now it jump to 2nd position. The cryptographic failure can also cause a major data security risk in web applications.
A03:2021-Injection
OWASP Top 10 2021 Injection shift down to 2nd position. In the study, it is found that 94% of security measures can be a break-in during the injection. 33 Common Weakness Enumerations in this category are the second most frequent in the Application. Cross-Site Scripting (XSS –A07:2017) is also part of this risk factor in this update.
A04:2021- Insecure Design
A new category thread launched in OWASP 2021. The thread is mostly focused on design flaws. It happens mostly that the third-party user requests you for some design update in the original application this may cause a security risk.
A05:2021- Security Misconfiguration
Security Misconfiguration factor moved up by one position in 2021. Around 90% of web applications were tested for the misconfiguration risk factor. A04:2017- External XML Entities are now part of this A05 OWASP 2021.
A06:2021-Vulnerable and Outdated Components
OWASP 10 2017 Using Components With Known Vulnerabilities is here moved up at 6th position with a new name as Vulnerable and Outdated Components. Every organization should have some special criteria to update outdated components of applications to prevent security threats.
A07:2021- Identification and Authentication Failure
This is nothing but the Broken Identification 2017 Top 10 List. Here is include CWEs are more obvious for Identification Failure Threat.
A08:2021-Software and Data Integrity Failures
This is a new category to OWASP Top 10 2021. Insecure Deserialisation thread category from 2017 included in this category. His category mainly focused on software updates, CI/ CD, and incoming data without verifying its integrity and security. Common Vulnerability and Exposures/Common Vulnerability Scoring System (CVE/CVSS) mapped in this category (10 CWEs).
A09:2021- Security Logging and Monitoring Failure
As the name suggested this type of thread occurs during multiple logging or multiple user accounts available for a specific application. This error is not properly included in CVE/CVSS data. However, if a failure occurs in this category can majorly impact mainstream data, financial data, visibility, user interface, etc.
A010:2021-Service-Side Request Forgery
This security thread was added in OWASP Top 10 2021 from the Top 10 Community Survey (#1). The research information shows this thread is not much harmful or impactable to the application and comes with a relatively average rating as a risk factor.
Top vulnerabilities in Web Application V/S OWASP Top 10
As this is virtual age, many unrestricted and unexpected errors occur at any movement. Developers should be always ready to secure their web applications from various threads. Here in this article, we saw how OWASP gives its Top 10 security risk document to protect the application. Vulnerabilities can come in any form lets see how this security risk document divides the top vulnerabilities in the risk factors list.
The below figure will be helpful for you to understand the proof of concept and relates Top 10 Risk
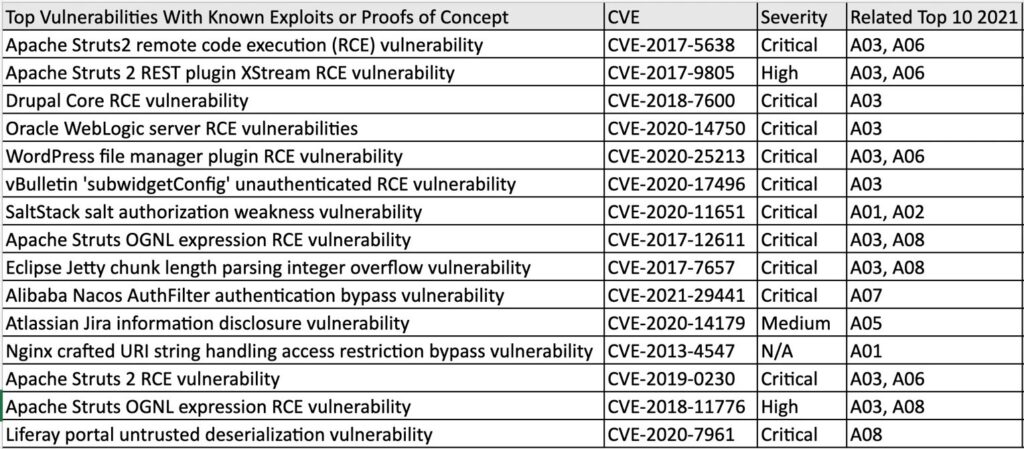
Here know about How to secure code via Web application Security testing and Risk factors
Securing data and code from these vulnerabilities is really a challenging thing when multiple users are working on it. In such a situation, a company or organization must apply TLS encryption on various communication modes and Logging.
In response to secure your application from vulnerabilities, the organization should impose a limitation on the number of users, exposed services, API endpoints, and ports.
There are some Code Security Verifications you should add to ensure your code is safe
1. Static Application Security Analysis (SATS) – Also known as “Security Code Review” or “Code Auditing” one of the best, quickest, and trusted verification tools.
2. Dynamic Application Security Analysis (DAST)- Dynamic analysis can only take place when the code is running. OWASP has its own dynamic application security analysis tool known as OWASP Zed Attack Proxy (ZAP).
3. Software Composition analysis (SCA)- This application tool is useful in checking outdated code or data. The OWASP has a tool to check old data is know as OWASP Dependency Check.
4. Runtime Application Self-Protection (RASP)- when you need to check your document instantly at run time this tool is really helpful. It protects real-time or immediate threat attacks.
Almost all old and updated security risks and vulnerabilities we have seen in this article. Secure your application on the web is not that easy one should help some tools to secure their code from attack.
Conclusion:
Your data on the web should be secure from build time to run time to protect that from attacks. Organizations such as OWASP provides this type of security to your application for free for more than 2 decades. Recently in September 2021, they launch their top 10 security risk measure known as OWASP Top 10 2021. We hope that this article is helpful for you to know details about OWASP’s Top 10 risk factors.